What happens when you type https://www.google.com in your browser and press Enter?
A General Description of How The Internet Functions
Have you ever wondered what happens behind the scenes when you type https://www.google.com in your browser and hit Enter? The process of loading a webpage is not a simple one-step process but rather a complex series of events. In my inaugural blog post, I will walk you through the different steps involved in loading a webpage and demystify the technical jargon.
1. DNS Request:
The first step is a DNS (Domain Name System) request. When you type in https://www.google.com, your browser does not load the requested webpage immediately. Instead, it sends a request to a DNS server to resolve or translate the human-readable name (google.com) to its associated IP (Internet Protocol) address, such as 142.250.65.174. The DNS request starts from your local machine’s cache memory and goes to your Internet Service Provider’s (ISP) cache memory. If it cannot find the IP address in these cache memories, the request is then redirected to the authoritative name servers. These DNS servers have all the IP addresses for all registered domain names. Your ISP receives the requested IP address, and it will forward it back to your browser. Your ISP and the local machine will save the IP address in their cache memory to speed up the DNS lookup process for the next time you visit.
2. TCP/IP:
The second step is establishing a TCP (Transmission Control Protocol) connection with the web server using the IP address obtained from the DNS request. TCP is a transport protocol that works on top of IP to establish a reliable connection between two devices and ensure reliable transmission of packets.
3. Firewall:
The third step is a firewall check. A firewall is part of a network security system that monitors incoming and outgoing network traffic based on predefined security rules. These security rules are used to allow or block specific traffic from attempting to enter your network, which keeps you safe from attackers or unwanted sites. A firewall can simply be thought of as a wall between your network and the internet. If google.com or any other site you want to visit is not blocked by a firewall, then it goes to the next step.
4. HTTPS/SSL:
The fourth step is checking whether the website is using the HTTPS (Hyper Text Transfer Protocol Secure) or HTTP (Hyper Text Transfer Protocol) protocol. If the website (google.com) is using an HTTPS connection, the browser sends a request for an SSL certificate to verify the identity of the website and to make the connection encrypted. This ensures that any sensitive data, like a bank account and password, will be kept safe. If the connection is HTTP, every communication between your computer and the web server can be sniffed.
5. Load Balancer:
The fifth step is checking whether the website (google.com) is using a load balancer. If it is, the load balancer distributes all the incoming network traffic to all servers based on the load balancing algorithm to reduce strain on a single server and speed up performance.
6. Web Server:
The sixth step is the web server accepting requests from the load balancer and sending the requested static webpage (of google.com) back to the browser. Web servers can serve static or dynamic content. If dynamic web content is requested, the request will be sent to the application server.
7. Application Server:
Application servers reside between web servers, which communicate with clients, and databases, which store application data. If the web server accepts dynamic content, the request is sent to the application server, and the application server serves the request. If it has to get the content from the databases, it does that.
8. Database:
The final step is the application server sending a query to the database if it needs to retrieve data. The database sends back the desired content to the application server, which then sends it to the web server and finally back to the client or browser.
The above steps represent a simplified version of what happens when you type a URL in your browser. It provides a good overview of the key components involved in the process. Now is the time to dig in and explore more about DNS and TCP. Let’s go then.
What is DNS? and How Does It Work?
Imagine you want to call your friend ‘Amy’. You take out your phone and start dialing her number, but you can’t remember the last four digits. What do you do? You check your phonebook, find the name ‘Amy,’ and call that contact. Your phone book translates the name ‘Amy’ to its associated phone number, which lets you make the call.
DNS works in a similar way. We humans aren’t able to memorize IP addresses like 142.250.185.206 or 2a00:1450:4001:827::200e to visit a website. It would be like trying to remember hundreds of phone numbers! Instead, we remember the domain names of websites, like google.com and yahoo.com.
When you type google.com into your browser and press Enter, your browser needs to know the IP address of the server that hosts the Google website. This is where DNS comes in. DNS resolves the domain name (google.com) to its corresponding IP address, like 142.250.185.206 or 2a00:1450:4001:827::200e.
But how does this translation process actually work? As you type a URL and press Enter, your browser starts a DNS request. It first checks its cache and the operating system cache to see if the IP address has been temporarily stored. If the IP address cannot be found in the cache, the browser sends a query to a DNS resolver, which is typically provided by your internet service provider (ISP).
DNS Resolution Process
a) DNS Resolver or Recursive Resolver:
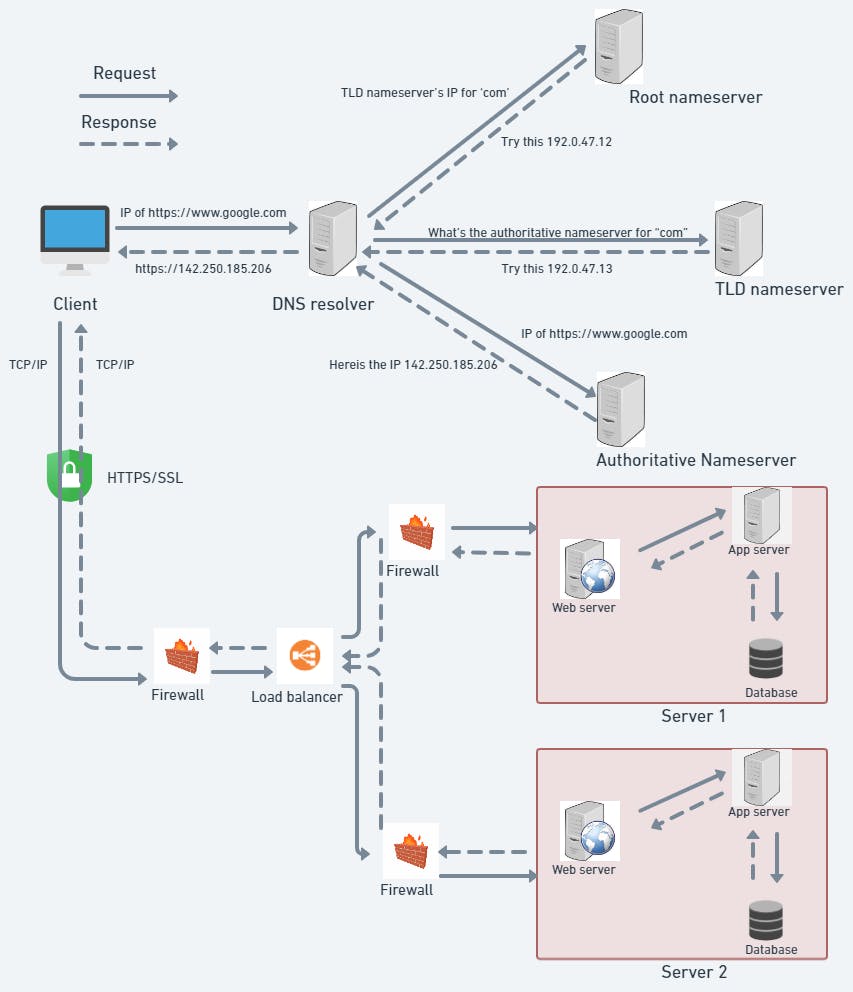
A DNS resolver, also known as a recursive resolver, is an intermediary device between the client’s browser and the DNS servers. The resolver has accepted a query for google.com from the above section, right? So it’s now going to check its DNS record to see if the recorded IPs in its cache match the fully qualified domain name (FQDN), which in our case is google.com. If the IP address is found, it will send it back to the browser, which will then render the page you were looking for. If there is no match, the query will be sent to the root nameserver.
b) Root Nameserver:
The root nameserver is the first step in the DNS hierarchy. When the query reaches the root nameserver, it identifies the Top-Level Domain (TLD) of the URL. In the case of google.com, the TLD is ‘.com’. The root nameserver does not know the IP address, but it will direct the resolver to the TLD nameserver for the ‘.com’ domain.
c) TLD Nameserver:
A TLD nameserver stores information about a domain’s top-level domains (TLDs), such as .com, .org, and .net. When the TLD nameserver receives a query from the DNS resolver, it will send back the location of the authoritative nameserver that has the matching IP address for https://www.google.com. The resolver will then send a query to the authoritative nameserver.
d) Authoritative Nameserver:
The authoritative nameserver is the final step in the DNS resolution process. All the necessary information regarding the domain name is stored on the authoritative nameserver. When the authoritative nameserver receives a query from the DNS resolver, it sends the IP address back to the resolver, which caches it for future use. The resolver then sends the IP address back to the browser, and the webpage is rendered.
The DNS resolution process is quick and happens in a blink of an eye. By understanding how it works, we can appreciate the important role that DNS plays in making the internet accessible.
The diagram below illustrates what happens when you type https://www.google.com in your browser and hit Enter.
What is TCP/IP?
TCP/IP is a set of communication protocols that connect network devices on the internet. It comprises two protocols: Transmission Control Protocol (TCP) and Internet Protocol (IP). While IP is responsible for addressing packets of data to be sent over the internet, TCP ensures that the packets are transported effectively using the assigned IP addresses. TCP establishes a reliable communication channel between the sender and receiver, ensuring that data is delivered in the correct sequence without any loss or corruption. Together, TCP and IP form the backbone of communication on the internet and enable seamless transmission of data across different networks.
The OSI And TCP/IP Model
The Open System Interconnection (OSI) model is the first standard network model for communication. It describes the seven layers used to communicate between network devices on the internet. Although it is a traditional and conceptual model, understanding how it works can make it easier to troubleshoot networking problems. However, the modern and practical network model is the TCP/IP model, which is more widely used today. The updated TCP/IP model uses five networking layers, which are compared to the OSI model in the table below for better understanding.
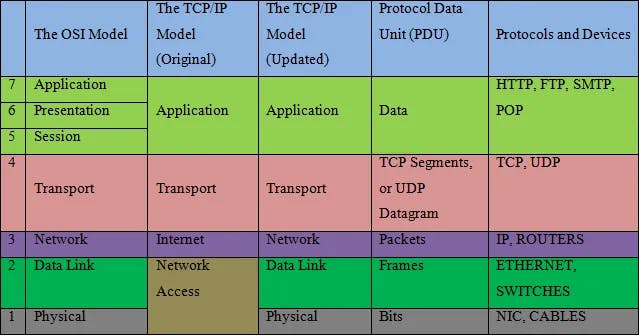
The Seven Layers of the OSI Model Explained
1) Application Layer:
The application layer is a crucial layer in the OSI and TCP/IP models that enables the communication between network applications and end-users. This layer is responsible for providing various protocols to send and receive data over the internet. Commonly used applications, such as web browsers like Chrome and Firefox or email clients like Outlook, operate at this layer.
The protocols used at this layer include HTTP (Hyper Text Transfer Protocol), which is used to transfer web pages; FTP (File Transfer Protocol), which is used for transferring files between devices; and SMTP (Simple Mail Transfer Protocol), which is used for sending email messages. POP (Post Office Protocol), which is used for receiving email messages; DNS (Domain Name System), which is used for translating domain names into IP addresses; and TELNET, which is used for remote access to network devices.
- Presentation Layer:
The presentation layer is a crucial component of the OSI and TCP/IP models responsible for data translation, compression, and encryption. Once data is received from the application layer, it needs to be converted from the human-readable format of characters and numbers into a binary format that can be transmitted over the network. This process is known as data translation. After translation, the data is compressed to reduce its size and enable faster transfer rates. Once compressed, the data is ready for transmission over the network.
If the data is using the HTTPS protocol, the final step is to encrypt it to ensure its confidentiality and integrity during transmission. Encryption involves transforming the data into an unreadable format that can only be deciphered with a private key known only to the receiver.
3) Session Layer:
The session layer is a vital component of the OSI and TCP/IP models responsible for establishing, managing, and terminating communication sessions between two network devices, such as a web browser and a web server, enabling them to exchange data.
In the TCP/IP model, the session layer, along with the presentation and application layers, are collectively referred to as the application layer. This layer is responsible for providing end-users with access to network applications and services, such as web browsing, email, and file transfer.
4) Transport Layer:
The transport layer is a critical component of the OSI and TCP/IP models that provide end-to-end communication between network devices. It receives data from the session layer and breaks it into smaller segments for transmission. At the receiving end, it reassembles these segments to reconstruct the original data.
The two transport protocols commonly used are Transmission Control Protocol (TCP) and User Datagram Protocol (UDP). TCP establishes a connection between two computers through a process called a three-way handshake. The handshake involves the exchange of SYN, SYN-ACK, and ACK packets between the client and the server, as can be seen in the figure below.
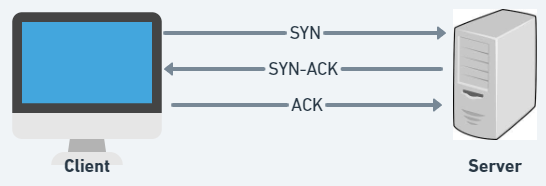
In the first handshake, the client sends its own sequence number in the SYN packet. The server then chooses its own sequence number and acknowledges the client’s sequence number in the second SYN-ACK packet’s handshake. The third handshake involves the client approving the server’s sequence number with an ACK packet. Once the handshakes are complete, TCP breaks the data into segments and sends them to the server over its IP.
TCP is more reliable than UDP because it provides error control, flow control, and sequence numbers. Error control is achieved through checksums, acknowledgments, and timeouts. Flow control ensures that the receiver can handle the data being transmitted, and sequence numbers help the receiver reassemble the segments in the correct order.
5) Network Layer:
The network layer is responsible for routing packets received from the transport layer. In this layer, TCP segments are divided into smaller packets for transmission. The packets are then sent and reassembled at the receiving end.
The Internet Protocol (IP) is commonly used for routing at the network layer. IP provides a logical addressing scheme that uniquely identifies each device on the network. When a packet is sent to its destination, the IP address is used to route it through the network to the correct destination device.
6) Data Link:
The data link layer is responsible for establishing, maintaining, and terminating a connection between devices. In this layer, packets received from the network layer are broken up into smaller units called frames, which are then transmitted to their destination.
The data link layer is composed of two sublayers: Logical Link Control (LLC) and Media Access Control (MAC). The LLC is responsible for identifying the network protocol in use, error checking, and synchronizing frames. On the other hand, the MAC address is used to identify the devices on the network and to allow for the transmission of data in and out.
7) Physical Layer:
The physical layer is the first and lowest layer in the OSI and TCP/IP network models. This layer is responsible for transmitting raw bits of data over a communication channel, such as physical cables or a wireless network. The layer defines the hardware, electrical, and physical aspects of the communication.
The physical layer takes the frames from the data link layer and converts them into a stream of bits to be transmitted over the network. It also receives the incoming bit stream and converts it back into frames to be passed to the data link layer for further processing.
You have seen that the OSI (Open Systems Interconnection) model and the TCP/IP (Transmission Control Protocol/Internet Protocol) model are two different models used for networking. The OSI model has seven layers, while the TCP/IP model has five layers. The OSI model is conceptual and traditional, whereas the TCP/IP model is more commonly used in practice.
Conclusion
In summary, this blog post explains the series of events that happen behind the scenes when a user types a URL like https://www.google.com into their browser and presses Enter. The process is not simple and includes multiple steps such as a DNS request, establishing a TCP connection, a firewall check, an HTTPS/SSL check, load balancing, a web server, an application server, and a database. The blog post explains each step in detail and also covers what DNS is and how it works. In addition to that, it covers the OSI and TCP/IP models to understand how networking works. The post serves as a helpful guide for people interested in understanding the technical side of webpage loading.